Digital estates no longer stop at the edge of the network. Anyone who has dealt with a brand impersonation case, a leaked API key or a fraudulent mobile app already knows this. The problem is not new. What has changed is the scale and the speed.
DRP Tools, short for digital risk protection, sit in the uncomfortable space between what an organisation controls and what still harms it. They do not secure servers or endpoints. They watch everything else. Domains you never registered. Social media accounts you never created. Cloud buckets you never knew existed.
That distinction matters more than most security programmes admit.
What DRP Tools Actually Do, in Practice
There is a tendency to describe digital risk protection in abstract terms. External threats. Brand monitoring. Threat intelligence. None of that reflects how these tools are used day to day.
In practice, DRP Tools spend most of their time doing unglamorous work. They enumerate lookalike domains. They scan app stores. They crawl marketplaces and paste sites. They watch social platforms for early signs of abuse. Not alerts. Patterns.
The value is not the detection itself. It is the ability to see risk forming before it turns into an incident ticket. Security teams rarely get that luxury elsewhere.
This is why DRP Tools tend to live slightly outside the SOC. They feed it, but they do not behave like traditional detection controls. They deal with intent, impersonation and misuse rather than exploitation.
Why Traditional Security Controls Miss This Entirely
Most security tooling assumes ownership. You patch what you run. You monitor what you deploy. You harden what you configure.
Digital risk does not respect that boundary.
A phishing domain using your brand does not touch your infrastructure. A fake executive profile on LinkedIn does not trip an EDR rule. A cloned mobile app distributing malware has no reason to interact with your network at all.
This is why organisations often notice these issues late. Usually through customers. Sometimes through regulators. Almost never through internal data.
DRP Tools exist because perimeter thinking still dominates security architecture, even when the perimeter has dissolved.
The Digital Risk Protection Flow
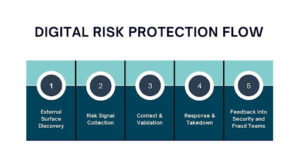
Below is the detailed digital risk protection flow:
External Surface Discovery
Mapping domains, subdomains, social accounts, mobile apps, code repositories, marketplaces. Most of it unauthorised. Some of it malicious. All of it external. This step focuses on building a continuously updated view of everything that represents the organisation outside its perimeter.
Risk Signal Collection
Looking for indicators that suggest misuse. Typosquatting. Brand abuse. Credential exposure. Executive impersonation. Fraud infrastructure reuse. These signals rarely exist in isolation and often emerge gradually across multiple platforms and services.
Context & Validation
Separating noise from intent. This step is where most value is created and where weak DRP deployments fail quietly. Many external signals are ambiguous by default and only become meaningful when enriched with context such as targeting, timing and reuse patterns.
Response & Takedown
Engaging registrars, platforms, hosting providers. Sometimes law enforcement. Sometimes legal. Often slow. Occasionally immediate. Success depends heavily on established relationships, evidence quality and jurisdictional realities. Even when takedown is delayed, coordinated response can still limit impact and prevent recurrence.
Feedback into Security and Fraud Teams
Improving awareness, controls and customer communications based on what is actually happening outside. External findings often reveal gaps that internal telemetry cannot, informing better detection logic and preventive controls. Over time, this feedback loop helps teams shift from reactive cleanup to proactive risk reduction.
This loop never really closes. It just keeps moving.
Where DRP Tools Fit Organisationally
One of the more awkward questions is ownership.
Digital risk protection touches security, fraud, legal, brand and sometimes marketing. No single team owns all of it. This is why DRP Tools are often underused even when they are technically deployed.
Security teams care about phishing infrastructure and credential abuse. Legal teams care about trademark violations. Fraud teams care about payment redirection and scams. DRP Tools sit in the overlap.
When they work well, they reduce friction between these groups. When they do not, they become another dashboard no one checks after the first quarter.
Common Mistakes When Deploying DRP Tools
The most common mistake is expecting immediate ROI. Digital risk does not spike on a schedule. It accumulates quietly.
Another mistake is over-automating takedowns without validation. False positives damage credibility with platforms very quickly. After that, response times stretch.
Finally, some organisations treat DRP Tools as a reporting exercise. Screenshots in board packs. Numbers without context. That is a missed opportunity. The real value lies in understanding how attackers adapt to your brand and behaviour.
Why This Matters More Than It Did Five Years Ago
Impersonation has become cheaper. Infrastructure spins up faster. AI-generated lures are more convincing, even if they are not particularly clever.
Attackers no longer need to breach a company to damage it. They just need to look like it for long enough.
DRP Tools are one of the few ways to see that happening in near real time.
Conclusion
Digital risk protection is not about owning more security tools. It is about accepting that risk lives well beyond what you manage directly. DRP Tools make that risk visible, but visibility alone is not enough.
You need people who understand how external threat ecosystems behave. Who know when to escalate, when to wait and when a takedown will do more harm than good.
CyberNX can help here. They utilize trusted, advanced and latest DRP tools to provide end-to-end DRP services. Not just monitoring, but real response. Real judgement. The kind that comes from seeing the same patterns repeat under different brand names.
Because the hardest risks to manage are usually the ones you do not technically own.
READ ALSO: How an Investment Calculator in India Helps Choose Best Investment Options





